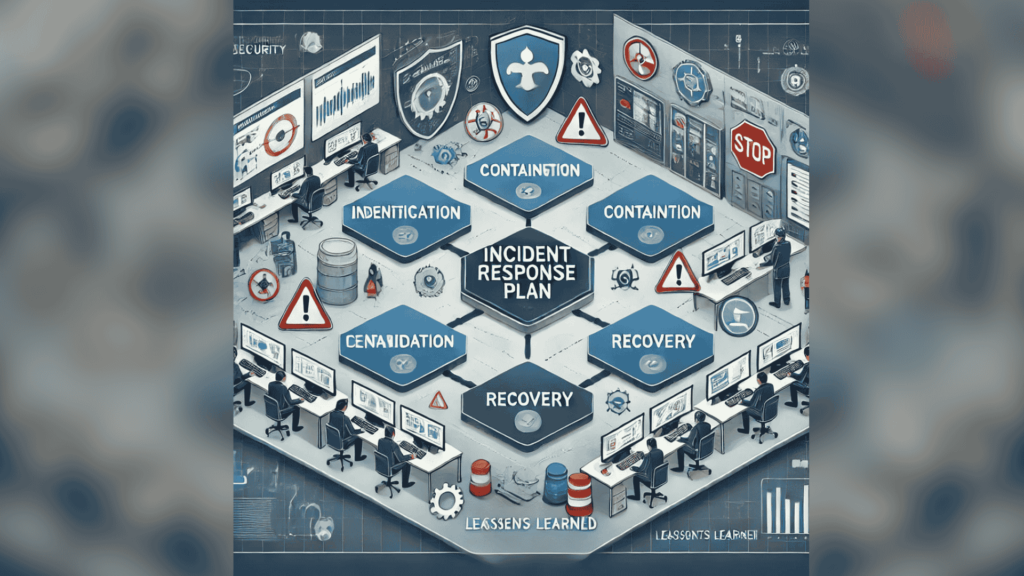
In today’s digital landscape, cyberattacks are no longer a question of if but when. Organizations must be prepared to respond swiftly and effectively to mitigate damage and restore operations. An incident response plan (IRP) is a structured approach to managing and addressing cybersecurity incidents, ensuring minimal disruption and protecting sensitive information. Here, we outline the key steps to create and execute an effective incident response plan.
Understand the Importance of an Incident Response Plan
An incident response plan provides a roadmap for handling cybersecurity incidents, enabling organizations to respond methodically rather than reactively. A well-crafted IRP helps minimize downtime, reduces the impact on operations, and ensures compliance with regulatory requirements. Additionally, it fosters a culture of preparedness, making it easier to address vulnerabilities and prevent future incidents.
Step 1: Preparation
Preparation is the foundation of any incident response plan. This step involves assembling an incident response team (IRT) comprising IT professionals, cybersecurity experts, legal advisors, and communication specialists. The team should be trained to handle various types of incidents, from phishing attacks to ransomware. Additionally, organizations should invest in tools like intrusion detection systems, endpoint protection software, and secure backup solutions to strengthen their defenses. Regular training and simulations ensure that the team remains ready to act.
Step 2: Identification
The identification phase focuses on detecting and verifying potential incidents. Organizations must establish monitoring systems to detect anomalies, such as unusual network activity or unauthorized access attempts. Once an incident is detected, the IRT should determine its scope, impact, and severity. Clear communication channels must be in place to ensure that the team can respond promptly to alerts and escalate the issue as needed.
Step 3: Containment
Containing the incident is critical to preventing further damage. This step involves isolating affected systems or devices to stop the spread of the attack. Depending on the severity, containment may be short-term (e.g., disconnecting a compromised device) or long-term (e.g., implementing firewall rules to block malicious traffic). The goal is to limit the attacker’s reach while preserving evidence for further investigation.
Step 4: Eradication
Once the incident is contained, the next step is to eliminate the threat. This involves removing malware, closing vulnerabilities, and patching systems to prevent a recurrence. Detailed logs and forensic analysis can help identify the root cause of the incident, ensuring that similar attacks can be thwarted in the future.
Step 5: Recovery
Recovery focuses on restoring normal operations as quickly and safely as possible. This includes reinstalling clean systems, restoring data from backups, and monitoring systems for signs of residual threats. The IRT must validate that all affected systems are secure before they are brought back online. A phased recovery approach can minimize the risk of reinfection.
Step 6: Lessons Learned
The final step involves a thorough review of the incident and the response process. The IRT should document what happened, what actions were taken, and what could be improved. This post-incident analysis helps organizations refine their IRPs and strengthen their defenses. Sharing insights and best practices across the organization can also enhance overall cybersecurity awareness.
Conclusion
An incident response plan is an essential component of any cybersecurity strategy. By following these structured steps—preparation, identification, containment, eradication, recovery, and lessons learned—organizations can effectively mitigate the impact of cyberattacks and build resilience against future threats. In the face of evolving cyber risks, preparedness and a proactive mindset are key to safeguarding digital assets and maintaining trust in a connected world.





